Your Using Outdated Linsence File Ragnarok
Take a trial with free scanner to check if your system is infected by Ragnarok ransomware
For more information, read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. The scanner you download here is free version and is able to scan your system for possible threat’s presence. however, it requires a 48 hour period to remove detected threats without any charge. if you want not to wait for that period, you will have to purchase its licensed version.
Ragnarok copies its file(s) to your hard disk. File name typical to Ragnarok is (.). Then it runs itself and creates new startup key in registry with name Ragnarok and value (.). If you will look into running processes list you will see some extra process with name like (.) or any random name that uses decent amount of your CPU. Update outdated license files from your command line - sungwoncho/license-up. Replacement for Gravity's RO patcher. Works faster and doesn't consume your entire memory for just seeing it crashing, aside from this, it works almost exactly as the official patcher does, so that it shouldn't break, unless Gravity changes something vital to their patcher. It is free of any cost and works on every 32-bit and 64-bit Microsoft. Windows. platform.
Tips To Restore Files from Ragnarok ransomware
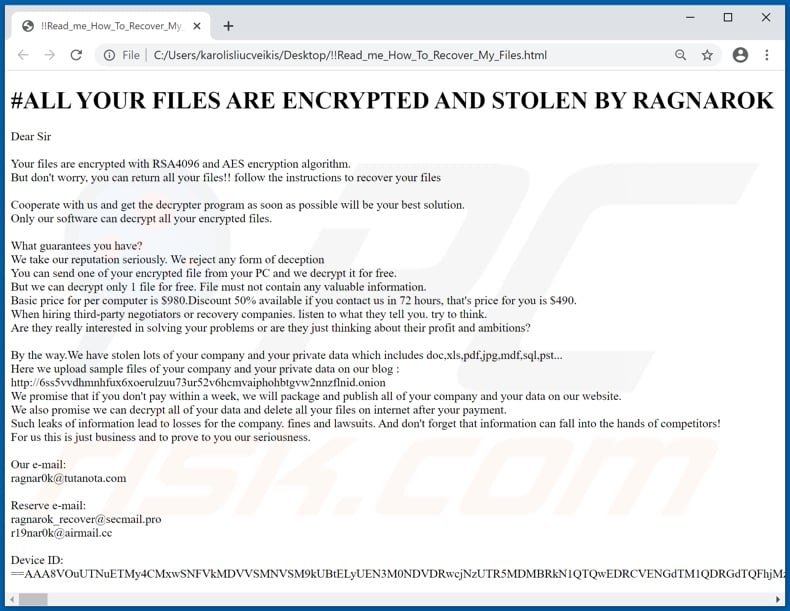
Ragnarok ransomware is a file encrypting virus that belongs to the ransomware family. It is mainly designed to lock down the target System and encrypt all types of personal and System files as well as force the victim to pay ransom money. It is able to easily invade all version Windows Based Operating system including the latest version Windows 10. It gets inside into the target system without any users knowledge with the spam email attachments and other tricky ways. Once gets inside into the targeted PC successfully, then it starts to encrypt all personal and system files of the compromised system by using a powerful encryption algorithm AES and RSA. After that it makes all the files totally inaccessible for the users by renames their file names by appending “.ragnarok_cry” extension. That is why victims are unable to open even single file as earlier. While victim try to open even single file then the ransom note “How_To_Decrypt_My_Files.txt” appears on the system screen which demands ransom money.
The ransom note “How_To_Decrypt_My_Files.txt” contains a text message which states that victim’s personal and system files including word, documents, text, images, photos, videos, audios have been encrypted but not damaged. So it is possible to restore data and files to their original condition if a decryption key is purchased from the cyber-criminal within two days. Otherwise it will delete and encryption is impossible. In order to receive decryption key victim have to paid unspecified money. In order to know how to purchase the decryption key and other more information victim are highly advice to send an email to the cyber-criminal by using the provided email address. Payment must be paid in the form of bitcoins within 48 hours to the wallet address within. They also warn victim if they will try to open files by using third party recovery software then their data and file will delete permanently. Victim can send upto 2 files for the testing of decryption is possible. The file should not contain any valuable data and not exceed from 1 MB.
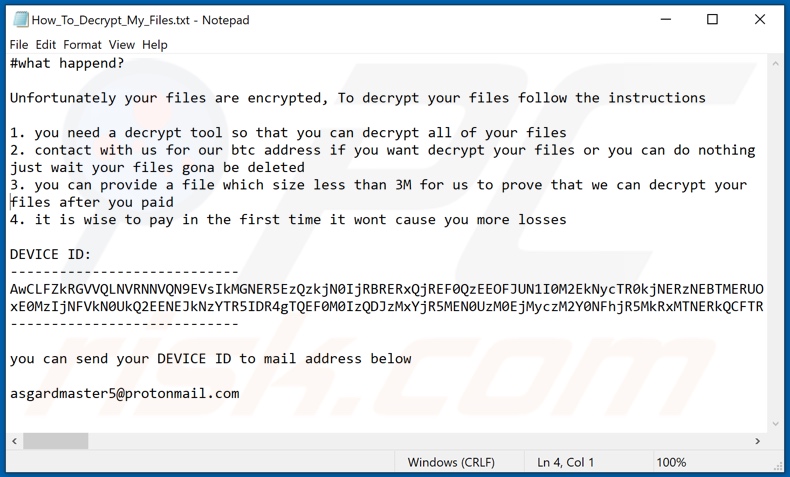
Text presented in Ragnarok ransomware text file (“How_To_Decrypt_My_Files.txt”):
#what happend?
Unfortunately your files are encrypted, To decrypt your files follow the instructions
- you need a decrypt tool so that you can decrypt all of your files
- contact with us for our btc address if you want decrypt your files or you can do nothing just wait your files gona be deleted
- you can provide a file which size less than 3M for us to prove that we can decrypt your files after you paid
- it is wise to pay in the first time it wont cause you more losses
DEVICE ID:
—————————-
–
—————————-
you can send your DEVICE ID to mail address below
Should I Pay Ransom Money:
Paying money to the hacker is highly risky for the victim because there is no any proof cyber-criminal will send original decryption key after received ransom money. So there are highly probability, received decryption key cannot open your files. In this way, you can loss their files and money as well. It may disable your anti-virus program to make your system weaker. So this virus does not want you to recover your files through any other method.
What to do when your PC got infected with Ragnarok ransomware
If your PC got infected with Ragnarok ransomware then do not need to panic. You can restore data by the using backup, volume shadow copy and using third party recovery software or tool. But before perform this activities you have to completely remove Ragnarok ransomware without any delay at the first detection by the using reputable antimalware tool.
How did Ragnarok ransomware gets installed into your System?
Ragnarok ransomware is commonly gest installed into the System via spam email campaign, fake updaters, downloading unwanted program from untrustworthy sources. Spam email campaign often used by the cyber-criminal to send thousands of email which contains malicious files or linked. The mail seems important, official, urgent and similar. The attachments files comes in various format like as archive, exe, PDF, MS office, documents, java scripts etc. when these files are opened then the hidden malicious program executed into the system. Update the System software from irrelevant sources like as torrent, emule and other sources cause the infiltration of lots of infections. Downloading freeware program from unofficial site without read their terms and license agreements. They also skip custom or advance options as well as other similar setting, thus this behavior offers to download and install unwanted program which leads lots of infections.
How To Protect your System from Ragnarok ransomware :
Do not open suspect email especially which received from unknown sender. If any attachment looks suspicious do not open them. If you do not know the sender name and address please try to know the sender. Must check the grammatical error and spelling mistakes of the content body before opening them. Users must update the System from relevant sources. Users are highly recommended try to download and install especially freeware program from third party webpage. Read the installation guide carefully till the end. Don’t Skip custom or advance options as well as other similar setting. Be pay attentive while clicking on malicious links, visiting commercial site because such types of activities also offers to install other unwanted program. Keep the System safe and secure victim are highly advice scan the PC regularly with a genuine antimalware tool.
Threat Summary:
Name: Ragnarok ransomware
Threat Type: Ransomware, Crypto Virus, Files locker.
Encrypted Files Extension: .ragnarok_cry
Ransom Demand Message: How_To_Decrypt_My_Files.txt
Cyber Criminal Contact: [email protected]
Distribution methods: Infected email attachments (macros), torrent websites, malicious ads.
Damage: All files are encrypted and cannot be opened without paying a ransom. Additional password-stealing trojans and malware infections can be installed together with a ransomware infection.
Recovery files : in order to recover files we are highly recommended to remove Ragnarok ransomware by using a reputable antimalware tool.
To restore encrypted files on your machine, you can take a trial with a suggested data recovery tool to check if it can help achieving your files back.
[Tips & Tricks]
- How to remove Ragnarok ransomware and related components?
- How to recover files encrypted by ransomware?
One thing is clear now that ransomware virus like Ragnarok ransomware is capable encrypting all types of files stored in your machine and makes them inaccessible. After complete encryption process, it attempt to generate monetary profit by offering bogus data recovery service. It is not good to pay demanded extortion money to cybercriminals for data recovery. You don’t waste your money and time on their fake service related to file recovery. We recommended you to avoid their bogus service and stop paying any amount of extortion money to them. Before you execute the various steps as solution, you have to take certain steps like backup the files, make sure this instruction page always open so that you can easily execute the steps as mentioned below and be patient with each step.
Procedure 1: Remove Ragnarok ransomware from System manually
Procedure 2: Remove Ragnarok ransomware and all the related components from computer automatically
Procedure 3: How to restore files encrypted by Ragnarok ransomware
It is possible to delete Ragnarok ransomware related components from computer with our easy solution. To do this, you have two methods of ransomware removal i.e., manual and automatic method. When we talk about manual method, the process includes various removal steps and requires technical expertise. Manual method of malware removal is time consuming process and if any mistake done in implementation of steps, resultant in several other damages in your computer. So, you should follow manual process carefully and if not possible you to complete the process, then you can go for automatic solution. Once the ransomware removed using these methods, you can go for third procedure i.e., data recovery procedure.
Procedure 1: Remove Ragnarok ransomware from System manually
Method 1:Restart the PC in Safe Mode
Method 2:Remove Ragnarok ransomware related process from Task Manager
Method 3:Delete Ragnarok ransomware malicious registries
Method 1: Restart the PC in Safe Mode
Step 1: Press “Windows + R” key from keyboard to open “Run” Window
Step 2: In the “Run” Window, you need to type “msconfig” and then press “Enter” key
Step 3: Now, select “Boot” tab and “Safe Boot”
Step 4: Click on “Apply” and “OK”
Method 2: Remove Ragnarok ransomware related process from Task Manager
Step 1: Press “CTRL + ESC + SHIFT” altogether to open “Task Manager”
Step 2: In the “Task Manager” Window, locate “Details” tab and search for all the malicious process related to Ragnarok ransomware.
Step 3: Right click on it and end the process
Method 3: Delete Ragnarok ransomware malicious registries
Step 1: Press “Windows + R” key from keyboard to open “Run” dialog box
Step 2: Type “regedit” command in text box and press “enter” key
Step 3: Now, press “CTRL + F” keys and type Ragnarok ransomware or the file name of malicious executable associated with malware. Usually, such suspicious files are located in “%AppData%, %Temp%, %Local%, %Roaming%, %SystemDrive% and so on.
Step 4: You should check the malicious files data by right click on the value. Detect all such suspicious registry objects in “Run” or “RunOnce” sub keys and delete them.
Procedure 2: Remove Ragnarok ransomware and all the related components from computer automatically
We have already discussed about manual method of Ragnarok ransomware removal using several methods. You can choose any methods as per your technical skills and PC requirements. If you are non-technical users, then it can be difficult to implements these steps completely so you can go for automatic solution. To remove Ragnarok ransomware and all the related components, you can use automatic method of malware removal. You should have powerful tool that has the ability to remove all components related to Ragnarok ransomware, unwanted registry entries and others.
Here, we are discussing about “SpyHunter” antivirus software that is designed to detect and delete all types of malware including Adware, potentially unwanted program (PUP), rootkits, browser hijacker, Trojan horse virus, backdoor, ransomware and others. “SpyHunter” security application is powerful anti-malware software that works on advance scanning mechanism to identify viruses quickly. It is inbuilt with enhanced multi-layer process that helps you search for all types of malware. If you searching for solution to remove Ragnarok ransomware and other related viruses during scanning process, then it is recommended to remove it soon.
How to download/ install and use “SpyHunter” security software?
Step 1: At first, you need to click on “Download” button to go to “SpyHunter” page
Take a trial with free scanner to check if your system is infected by Ragnarok ransomware
For more information, read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. The scanner you download here is free version and is able to scan your system for possible threat’s presence. however, it requires a 48 hour period to remove detected threats without any charge. if you want not to wait for that period, you will have to purchase its licensed version.
Step 2: After downloading, double click on “Installer” file to install this program on your System
Step 3: After complete installation process, open SpyHunter application and click on “Start Scan Now” button to start scanning process. For the first time, you should select “Full Scan” option
Step 4: Now, click on “View Scan Results” to see the list of detected threats or infections
Step 5: Click on “Next” button to register the software and remove permanently if you find Ragnarok ransomware and related infections.
Procedure 3: How to restore files encrypted by Ragnarok ransomware
Method 1:Recovery of files encrypted by Ragnarok ransomware using “Shadow Explorer”
Method 2: Recovery of files encrypted by Ragnarok ransomware using powerful data recovery software
Method 1: Recovery of files encrypted by Ragnarok ransomware using “Shadow Explorer”
“Shadow Volume Copies” are temporary backup files created by the OS for short span of time for all files and data that has been deleted or damaged recently. If there is “File history” enabled in PC, then you can use “Shadow Explorer” to retrieve the data. When we talk about advanced Ransowmare virus, it deletes the “Shadow Volume Copies” as well as prevents you from recovering the files and data with help of administrative commands.
Step 1: At first, you need to click on link given below to download “Shadow Explorer” on your computer
Step 2: Browse the location where the files has been downloaded.
Step 3: Double click on the ZIP files to extract the folder
Step 4: Click to open “ShadowExplorerPortable” folder and double click on the file.
Step 5: In order to select the time and data as per your requirement, a drop down menu appears on the screen. Select the files that you want to restore and click on “Export” button.
Method 2: Recovery of files encrypted by Ragnarok ransomware using powerful data recovery software
You should make sure that your System is free from ransomware attack and all the files associated with Ragnarok ransomware have been removed successfully. Once done, you should to go for data recovery solution. After complete ransomware related files removed, you can use “Stellar Phoenix Data Recovery Software” to retrieve the files. To restore encrypted files, you can follow the steps given below.
How to download/install and use “Stellar Phoenix Data Recovery Software”?
Step 1: At first, you need to click on download button to download Stellar Phoenix Data Recovery Software in your computer
To restore encrypted files on your machine, you can take a trial with a suggested data recovery tool to check if it can help achieving your files back.
Step 2: Once downloaded, double click on “installer file” to install
Step 3: Now, click on “I accept the agreement” in “License Agreement page” and click on “Next”
Step 4: After complete installation process, run the application.
Step 5: On the new interface, select the file types that you want to retrieve and then select “Next” button
Step 6: Now, select the “Drive” where you want the software to do scanning. Click on the “Scan” button
Step 7: Wait for the complete the process. It may take some times to complete process depending on the size of selected drives. After complete scanning process, you would notice a file explorer with the preview of data that can be recovered. You have to choose the files that you want to restore.
Step 8: Finally, choose the location where you want to save the restored files.
Prevention tips to protect your System from Ragnarok ransomware related attacks in future
- You should have strong backup of all files and data stored in your computer because some ransomware is designed to look for network shares and encrypt all files stored in your machine. You would do well to store data backups on secure cloud server with high-level encryption and multiple-factor authentication.
- Ransomware type virus often relies on exploit kits to gain illicit access to a System or network. If you run outdated or obsolete software on your computer, then you are in risk of ransomware because the software developers are not putting out security updates anymore. To remove abandonware and replace it with software still being supported by manufacturer.
- The cybercriminals behind ransomware attack are using former banking Trojan as delivery vehicle for ransomware. It relies on malspam to infect your System and get foothold on your network. Once it gain access to your network, it shows worm like behaviour spreading from System to System using list of common passwords.
- You should be alert while surfing online and avoid installing freeware from unknown sources, stop opening attachments coming from unknown emails and click on ads or popup messages after double reading.
- Don’t pay extortion money in case of attack. We recommended you to stop paying ransom and FBI agrees. Cybercriminals don’t have scruples and there is no guarantee you will get files back. By paying extortion money, you are showing cybercriminals that ransomware attack work.
RAGNAROK ransomware on a rise in 2020
Contents
- RAGNAROK ransomware on a rise in 2020
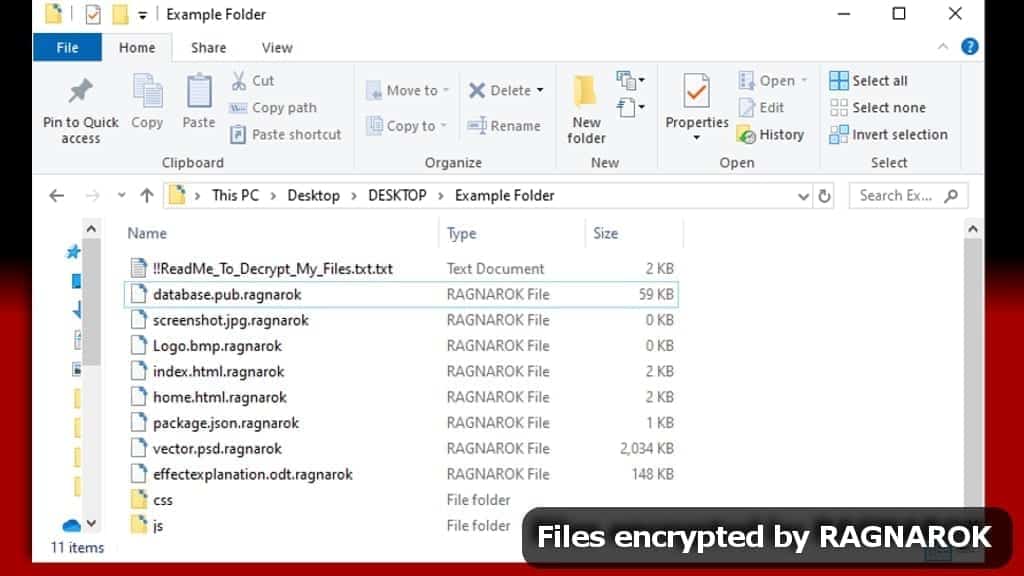
RAGNAROK is a malicious ransomware-type virus which encrypts files on victim’s computer. The data encryption restricts access to these files. The virus marks affected files with .ragnarok extension and leaves a ransom note called !!ReadMe_To_Decrypt_My_Files.txt in every folder. The ransomware suggests contacting the attackers via [email protected], [email protected] or [email protected] to get a specific ransom price. The note threatens to make victim’s data public if the cybercriminals’ requirements aren’t followed.
RAGNAROK ransomware asks for approximately 1 Bitcoin for one infected PC, or 5 Bitcoins for computers on infected server. As specified in the ransom note, the attackers will specify an exact sum of money in Bitcoin after receiving victim’s ID.
Currently, there are no known ways to decrypt .ragnarok extension files for free. Victims who have data backups should remove the virus as soon as possible and restore data using external data storage devices.
Threat Summary
The behavior of the ransomware explained
Once executed on the target system, Ragnorak file virus first checks the language ID of Windows. It has a language exclusion list that shuts down the malicious process and doesn’t perform encryption if the victim’s PC is set to one of the listed languages:
- 0419 = Russia;
- 0423 = Belarus;
- 0444 = Russia;
- 0442 = Turkmenistan;
- 0422 = Ukraine;
- 042c = Azerbaijan;
- 0426 = Latvia;
- 043f = Kazakhstan;
- 0804 = China.
It must be noted that ransomware developers who are based in Russia or other CIS countries rarely exclude China.
If the ransomware detects any other language ID, it gives a greenlight for the attack to begin. The first thing that it does is attempt to disable Windows Defender by adding group policies in Windows Registry. The ransomware injects the following rules:
- HKLMSOFTWAREPoliciesMicrosoftWindows Defender “DisableAntiSpyware” = 1
- HKLMSOFTWAREPoliciesMicrosoftWindows DefenderReal-Time Protection “DisableRealtimeMonitoring” = 1
- HKLMSOFTWAREPoliciesMicrosoftWindows DefenderReal-Time Protection “DisableBehaviorMonitoring” = 1
- HKLMSOFTWAREPoliciesMicrosoftWindows DefenderReal-Time Protection “DisableOnAccessProtection” = 1
These attempts will be unsuccessful if the victim has Windows 10 Tamper Protection feature on.
Next, Ragnarok malware tries to delete Volume Shadow Copies (to prevent data recovery), then disables Windows auto startup repair feature, and turns off Windows Firewall by executing these commands via cmd:
- /c vssadmin delete shadows /all /quiet
- /c bcdedit /set {current} bootstatuspolicy ignoreallfailures
- /c bcdedit /set {current} recoveryenabled no
- /c netsh advfirewall set allprofiles state off
When the preparation tasks are completed, the ransomware begins data encryption. It uses AES encryption to generate the encryption key, which is then encrypted with a packed RSA4096 key. This ensures that only the virus’ developers can restore the encryption key.
The ransomware skips executive files, also .dll and .sys files, and the files that have already been encrypted by the virus (those with .ragnarok extension). As usual, the ransomware bypasses files essential for operating system to function.
The ransomware targets unpatched Citrix ADC servers
RAGNORAK virus is known to be targetting Citrix ADC servers with unpatched vulnerability which is known under CVE-2019-19781 code. Although the vulnerability is now patched, networks who fail to install the update are open to attacks and the said ransomware infection. The Citric vulnerability has also been exploited by Sodinokibi ransomware developers.
The EternalBlue vulnerability in Citrix ADC servers allow the attackers to perform arbitrary code execution remotely. In particular, the attacker can insert a specific DLL that is capable of downloading and launching Ragnorak ransomware payload on the computer or the whole computer network instantly.
Remove RAGNAROK ransomware virus safely
You must remove RAGNAROK ransomware virus and possibly related malware from your computer system as soon as possible. The easiest and safest way to root out such threats from Windows computer is by performing the removal in Safe Mode.
The tutorial below explains how to boot your PC in Safe Mode and run your security software from there. This will ensure a successful RAGNORAK removal.
When it comes to .ragnarok decryption, currently there are no tools that can recover files for free. In addition, we suggest being aware of scammers who might take your money and simply pay the ransomware developers instead of you. However, the security experts will keep investigating the virus and report back as soon as any routine flaws are noticed.
OUR GEEKS RECOMMEND
RESTORO provides a free scan that helps to identify hardware, security and stability issues and presents a comprehensive report which can help you to locate and fix detected issues manually. If you decide to purchase the full version of software, it will fix detected issues automatically and might revert certain virus damage to your system.
RESTORO uses AVIRA scanning engine to detect existing spyware and malware. If any detections are found, the software will eliminate them. Learn more about the software's features in its full review.
GeeksAdvice.com editors select recommended products based on their effectiveness. We may earn a commission from affiliate links, at no additional cost to you. Learn more.
RAGNAROK Ransomware Removal Guidelines
Method 1. Enter Safe Mode with Networking
Step 1. Start Windows in Safe Mode with Networking
Before you try to remove the virus, you must start your computer in Safe Mode with Networking. Below, we provide the easiest ways to boot PC in the said mode, but you can find additional ones in this in-depth tutorial on our website – How to Start Windows in Safe Mode. Also, see a video tutorial on how to do it:
Instructions for Windows XP/Vista/7 users
- First of all, turn off your PC. Then press the Power button to start it again and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. This launches the Advanced Boot Options menu.
- Use arrow keys on the keyboard to navigate down to Safe Mode with Networking option and press Enter.
Instructions for Windows 8/8.1/10 users
- Open Windows Start menu, then press down the Power button. On your keyboard, press down and hold the Shift key, and then select Restart option.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart.Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Networking. In this case, it is the F5 key.
Step 2. Remove files associated with the virus
Now, you can search for and remove RAGNAROK Ransomware files. It is very hard to identify files and registry keys that belong to the ransomware virus, Besides, malware creators tend to rename and change them repeatedly. Therefore, the easiest way to uninstall such type of a computer virus is to use a reliable malware removal program. In addition, we suggest trying System Mechanic Ultimate Defense, which includes data recovery tool and many other useful features.
Special Offer
RESTORO is a unique PC Repair Tool which comes with an in-built Avira scan engine to detect and remove spyware/malware threats and uses a patented technology to repair virus damage. The software can repair damaged, missing or malfunctioning Windows OS files, corrupted DLLs, and more. The free version offers a scan that detects issues. To fix them, license key for the full software version must be purchased.
Method 2. Use System Restore
In order to use System Restore, you must have a system restore point, created either manually or automatically.
Step 1. Boot Windows in Safe Mode with Command Prompt
Instructions for Windows XP/Vista/7 users
- Shut down your PC. Start it again by pressing the Power button and instantly start pressing F8 button on your keyboard repeatedly in 1-second intervals. You will see Advanced Boot Options menu.
- Using arrow keys on the keyboard, navigate down to Safe Mode with Command Prompt option and press Enter.
Instructions for Windows 8/8.1/10 users
- Launch Windows Start menu, then click the Power button. On your keyboard, press down and hold the Shift key, and then choose Restart option with the mouse cursor.
- This will take you to Windows Troubleshoot screen. Choose Troubleshoot > Advanced Options > Startup Settings > Restart.Tip: If you can't find Startup Settings, click See more recovery options.
- In Startup Settings, press the right key between F1-F9 to enter Safe Mode with Command Prompt. In this case, press F6 key.
Step 2. Start System Restore process
- Wait until system loads and command prompt shows up.
- Type cd restore and press Enter, then type rstrui.exe and press Enter. Or you can just type %systemroot%system32restorerstrui.exe in command prompt and hit Enter.
- This launches System Restore window. Click Next and then choose a System Restore point created in the past. Choose one that was created before ransomware infection.
- Click Yes to begin the system restoration process.
After restoring the system, we recommend scanning the system with antivirus or anti-malware software. In most cases, there won't be any malware remains, but it never hurts to double-check. In addition, we highly recommend checking ransomware prevention guidelines provided by our experts in order to protect your PC against similar viruses in the future.
Alternative software recommendations
Malwarebytes Anti-Malware
Removing spyware and malware is one step towards cybersecurity. To protect yourself against ever-evolving threats, we strongly recommend purchasing a Premium version of Malwarebytes Anti-Malware, which provides security based on artificial intelligence and machine learning. Includes ransomware protection. See pricing options and protect yourself now.
System Mechanic Ultimate Defense
If you're looking for an all-in-one system maintenance suite that has 7 core components providing powerful real-time protection, on-demand malware removal, system optimization, data recovery, password manager, online privacy protection and secure driver wiping technology. Therefore, due to its wide-range of capabilities, System Mechanic Ultimate Defense deserves Geek's Advice approval. Get it now for 50% off. You may also be interested in its full review.
Disclaimer. This site includes affiliate links. We may earn a small commission by recommending certain products, at no additional cost for you. We only choose quality software and services to recommend.
Norbert Webb is the head of Geek’s Advice team. He is the chief editor of the website who controls the quality of content published. The man also loves reading cybersecurity news, testing new software and sharing his insights on them. Norbert says that following his passion for information technology was one of the best decisions he has ever made. “I don’t feel like working while I’m doing something I love.” However, the geek has other interests, such as snowboarding and traveling.
Related posts:
Your Using Outdated Licence File Ragnarok Download
- Remove ESCAL Ransomware (Virus Removal Guide) ESCAL ransomware descriptionContentsESCAL ransomware descriptionRansom note contents explainedRansomware distribution and...
- Remove QEWE Ransomware Virus (2021 Decrypt Guide) QEWE ransomware virus attacks personal files to demand ransom in...
- Remove REHA Ransomware Virus (2021 Guide) REHA ransomware is the 199th variant of DJVU file-encrypting virusContentsREHA...